While many individuals are concerned about privacy in light of PRISM, some malicious actors are using the program to scare naive users into installing ransomware. Since August 23rd, our client Zscaler have seen about 20 domains that carry FakeAV and Ransomware. These websites seem to have been hijacked. They are all hosting the malicious content over port 972 and use similar URL patterns. Here are a couple examples:
- kringpad.websiteanddomainauctions.com:972/lesser-assess_away-van.txt?e=20
- miesurheilijaaantidiabetic.conferencesiq.com:972/realism_relinquish-umbrella-gasp.txt?e=21
- squamipi.worldcupbasketball.net:972/duty_therefore.txt?e=21
The malicious files seem to be changing. It started with the classic FakeAV, then switched to a fake PRISM warning. In both cases, the goal is to scare the target into paying the attacker to “fix” their computer.
FAKEAV
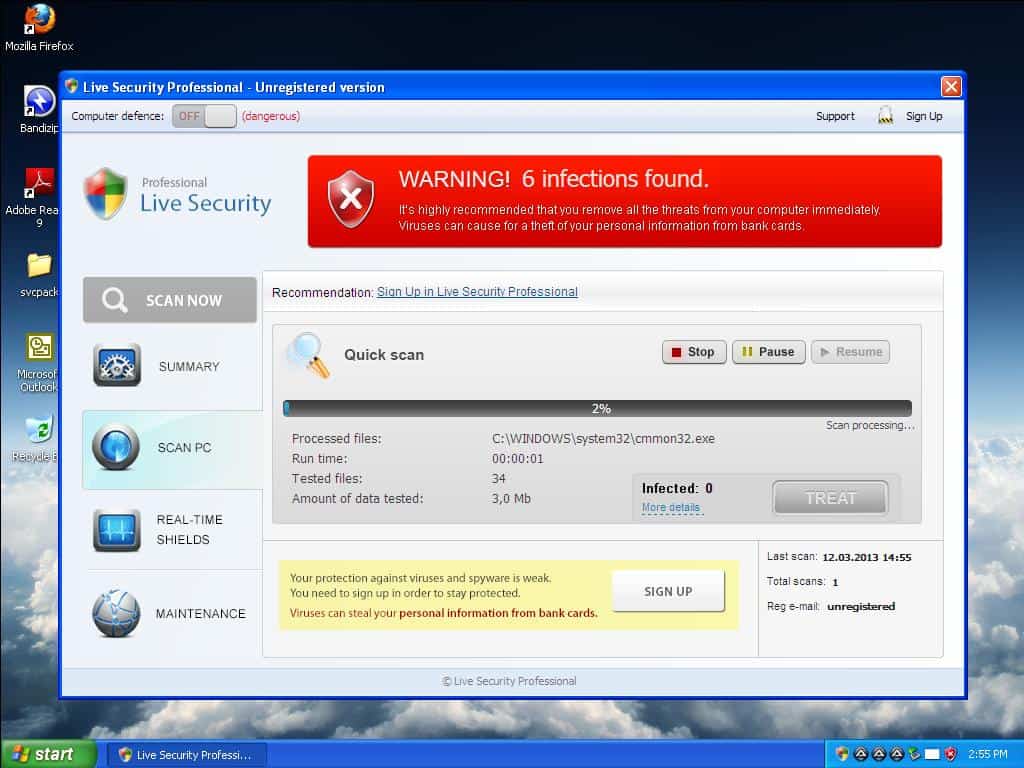
FakeAV remains a popular technique to lure targets into paying attackers. Most of the instances of FakeAV that Zscaler reported earlier were running a fake computer scan in the browser. This time it appeared as a Desktop application.
FakeAV scan of the computer
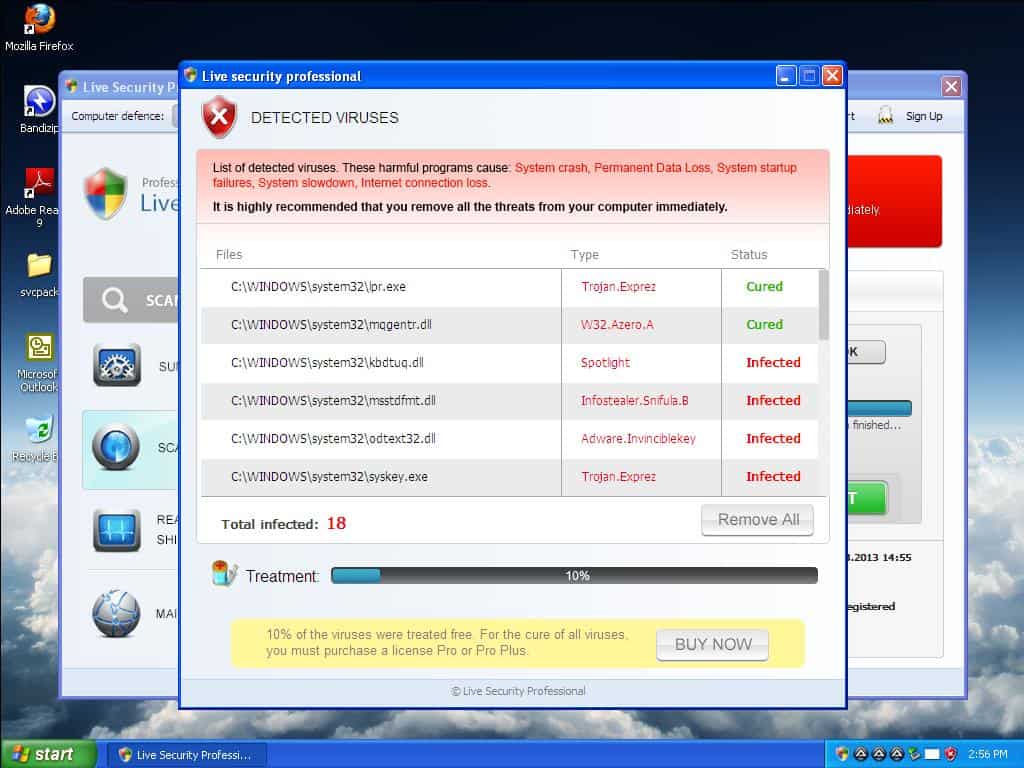
FakeAV claims to have found threats
The scan claims to have found 18 threats. Two have been cured, but the victim must pay to get the remaining 16 threats taken care of.
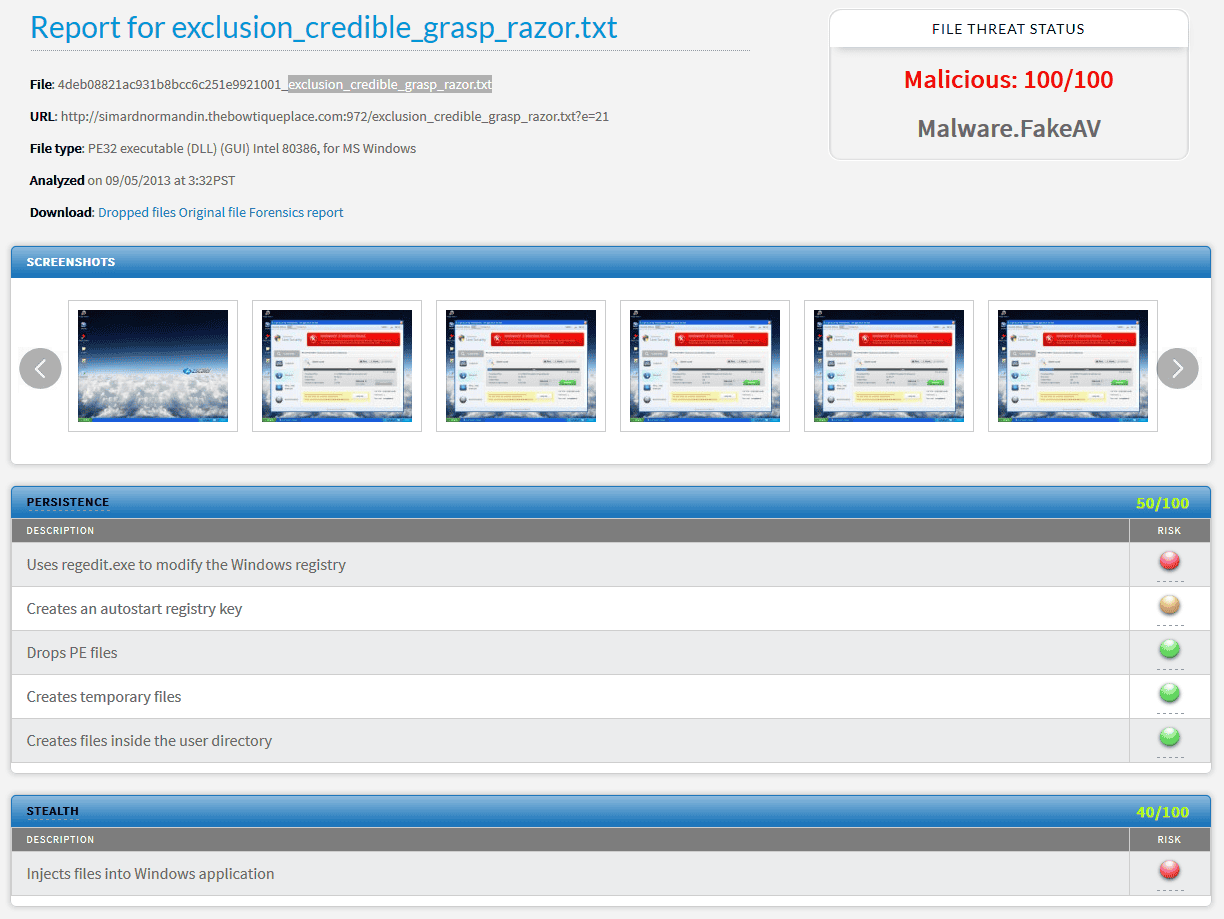
Some of the malicious behaviors of this FakeAV variant
PRISM WARNING
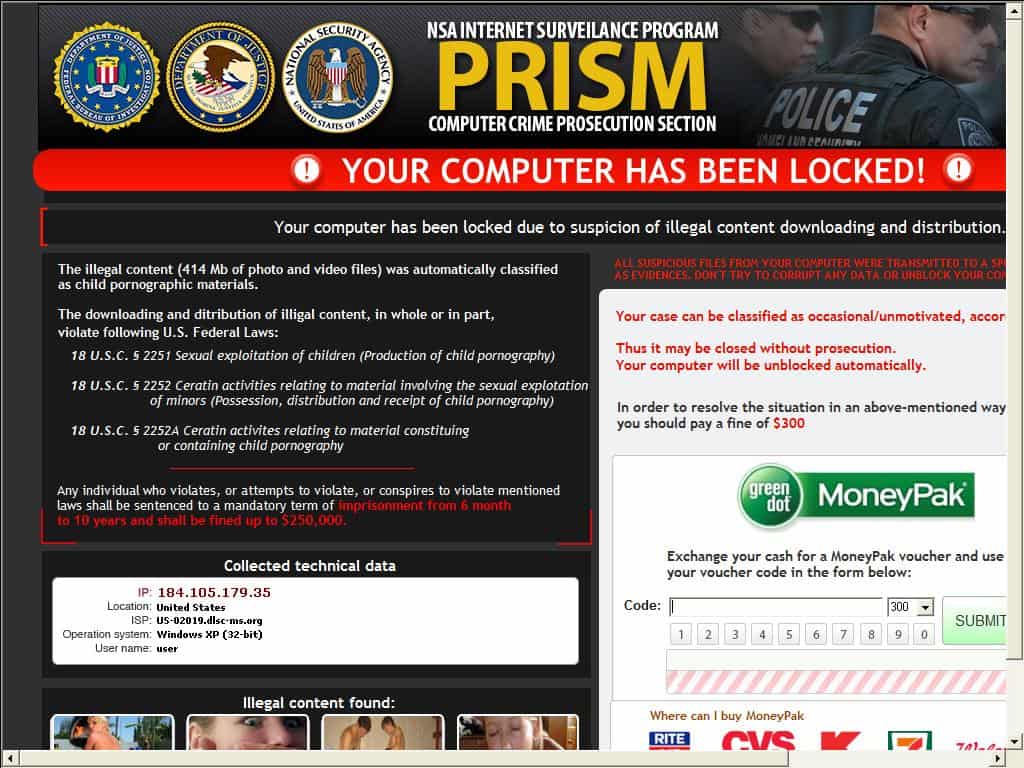
The other malware is interesting. The attacker uses the recent news about PRISM to claim that the victim’s computer has been blocked because it accessed illegal pornographic content. The victim has to pay $300 through MoneyPak, a prepaid card service.
Victim needs to pay up $300 to get his computer back.
Zscaler expect attackers to take advantages of the upcoming UK laws on accessing adult content online to send new types of fake warnings to UK victims.
– LARA LACKIE